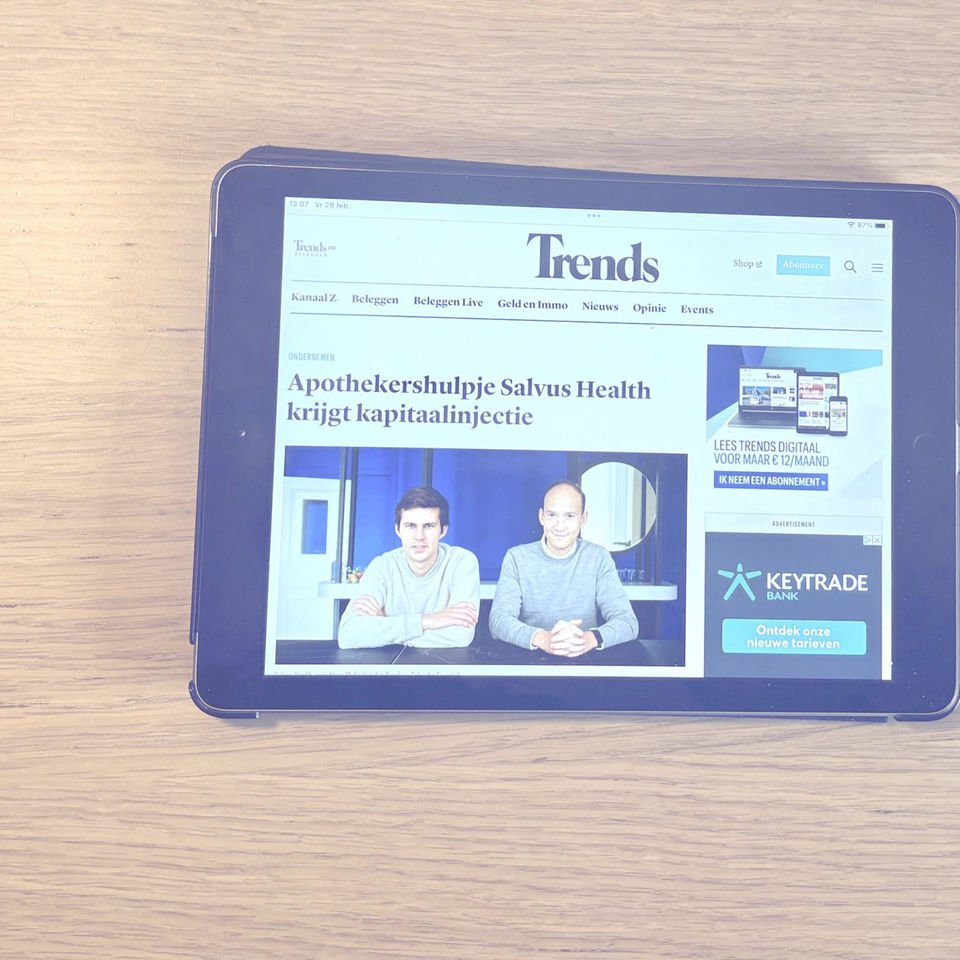
Make the news
Freelance PR services for fast-growing Tech companies

Customers
Comiti PR
Pantheonlaan 65
1081, Brussels
info(@)comiti.be
+32 4 98 29 13 14

About
Founded by Rodrigue Delépine, Comiti is a freelance native (FR/NL) Brussels-based public relations consultancy, specialized in IT, Tech and startup PR.
Whether you're a multinational or a startup eager to grow your business in Flanders, Brussels or Wallonia, I will tell your story to the right journalists and media.
They made the news
Rodrigue showed his thorough knowledge of the Belgian media during the PR workshop.
Louis Liekens
Marketing Manager
IsoHemp
The follow up, the service, the PR results... Everything is there.
Laura Baudinet
Marketing Manager
Horus Software
Seeing our company in the media is so rewarding.
Eric de Roest
Owner
Wide Open
Services
Startup growth
Doing PR is one of the most (cost-)effective ways to quickly reach wider audiences and gain trust from the market. Your startup growth story can be tomorrow’s headline.
Expertise in Tech & IT
From AI to hybrid cloud, understanding the complex IT landscape is crucial to delivering the right messages to the specialized IT and Tech press.
Native communications
Go for a local, multilingual partner (French and Dutch) who understands the cultural differences and can communicate your message in the other linguistic community.
Corporate positioning
Grow your company by understanding your ideal customer and his behaviour. Know how you are perceived by your customer base and how you should adapt to it.